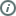What Should I Know About Encryption?
Last Reviewed: January 01, 2025
Perhaps you've heard the word “encryption ” used, but in so many different contexts it’s gotten confusing. You might have seen it referring to everything from protecting your laptop, chat app security, or guarding your shopping online. Regardless of when it’s used, when we talk about encryption, we’re referring to the same thing: the mathematical process of making a message unreadable except to a person who has the “key ” to “decrypt ” it. From there, it gets more complicated.
People have used encryption to send messages to each other that (hopefully) couldn’t be read by anyone besides the intended recipient. Today, we have computers that are capable of performing encryption for us. Digital encryption technology has expanded beyond simple secret messages, and these days you can use encryption for more elaborate purposes, like not just hiding the content of messages from prying eyes, but also verifying the author of those messages.
Encryption is the best technology we have to protect information from bad actors, governments, and service providers. When used correctly it is virtually impossible to break.
In this guide, we’ll look at two major ways encryption is applied: to scramble data at rest and data in transit.
Encrypting Data At Rest anchor link
Data “at rest” is data that is stored somewhere, like on a mobile device, laptop, server, or external hard drive. When data is at rest, it is not moving from one place to another.
One example of a form of encryption that protects data at rest is “full-disk” encryption (also sometimes called “device encryption”). Enabling full-disk encryption encrypts all the information stored on a device and protects the information with a passphrase or another authentication method. On a mobile device or laptop, this usually looks like a device lock screen, requiring a passcode, passphrase, or thumbprint. However, locking your device (i.e., requiring a password to “unlock” your device) does not always mean that full-disk encryption is enabled.
|
|
|
A smart phone and laptop that each have a password-protected “lock” screen. |
Be sure to check how your operating system enables and manages full-disk encryption. While some operating systems have full-disk encryption enabled by default, some operating systems do not. That means someone could access the data on your device by bypassing device lock and accessing the hard drive directly, without needing to break the encryption key since the device itself is not encrypted. Some systems store unencrypted plaintext in RAM, even when you are using full-disk encryption. RAM is temporary storage, which means that after your device is powered down the memory typically can't be read, but a sophisticated adversary could attempt a cold boot attack and conceivably retrieve the RAM contents.
Full-disk encryption can protect your devices from people who have physical access to them. This is useful if you want to protect your data from roommates, coworkers or employers, school officials, family members, partners, police officers, or other law enforcement officials. It also protects the data on your devices if they are stolen or lost, like if you accidentally leave your phone on a bus or at a restaurant.
There are other ways to encrypt data at rest. One option, known as “file encryption,” encrypts only individual files on a computer or other storage device. Another option is “drive encryption” (also known as “disk encryption”) which encrypts all of the data on a specific storage area on a device.
You can use these different types of encryption at rest in combination. For example, let’s say you wanted to protect sensitive information on your medical documents. You can use file encryption to encrypt an individual medical file stored on your device. You can then use drive encryption to encrypt the part of your device that this medical information is stored on. Finally, if you have enabled full-disk encryption on your device, everything—all medical information as well as every other file on the drive, including the files for the computer’s operating system—is encrypted. So, even if someone figured out your computer’s login password, they would still need to also know the password you used to encrypt the file with your medical information before they could access it.
Check out our guides for enabling full-disk encryption on your computer, and iPhone or Android.
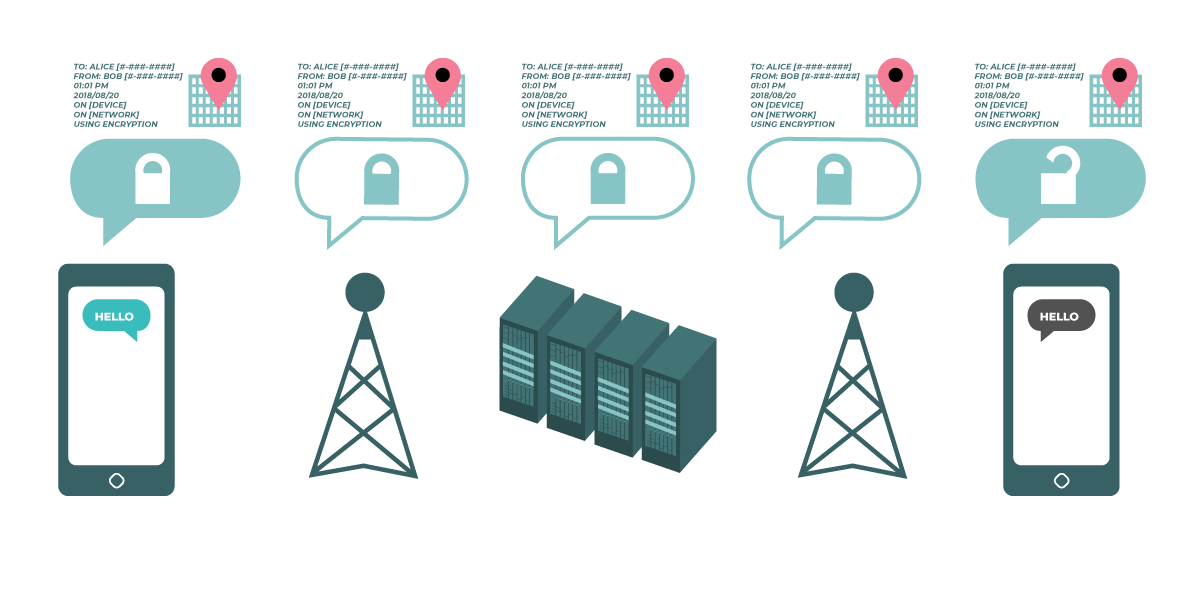
Encrypting Data In Transit anchor link
|
|
|
The diagram shows unencrypted data in transit. On the left, a smartphone sends a green, unencrypted message to another smartphone on the far right. Along the way, a cellphone tower passes the message along to company servers and then to another cellphone tower, which can each see the unencrypted “Hello” message. All computers and networks passing the unencrypted message are able to see the message. At the end, the other smartphone receives the unencrypted “Hello” message. |
Data “in transit” is information that is moving over a network from one place to another. For example, when you send a message on a messaging app, the message moves from your device, to the app company’s servers, and then to your recipient’s device. Another example is web browsing: when you go to a website, the data from that webpage travels from the website’s servers to your browser.
Some popular apps offer features that seem to protect messages, such as disappearing messages. However, depending on your security plan, disappearing messages may not provide the security properties you need. Just because a communication (like a chat or message) can feel secure, doesn’t mean it is secure. Computers passing along your message may be able to look at the contents of your message.
There are two ways to encrypt data in transit: transport-layer encryption and end-to-end encryption . The type of encryption a service provider supports can be an important factor in deciding what services are right for you. It’s important to know whether conversations are encrypted via transport-layer encryption or end-to-end encryption.
Transport-layer encryption anchor link
|
|
|
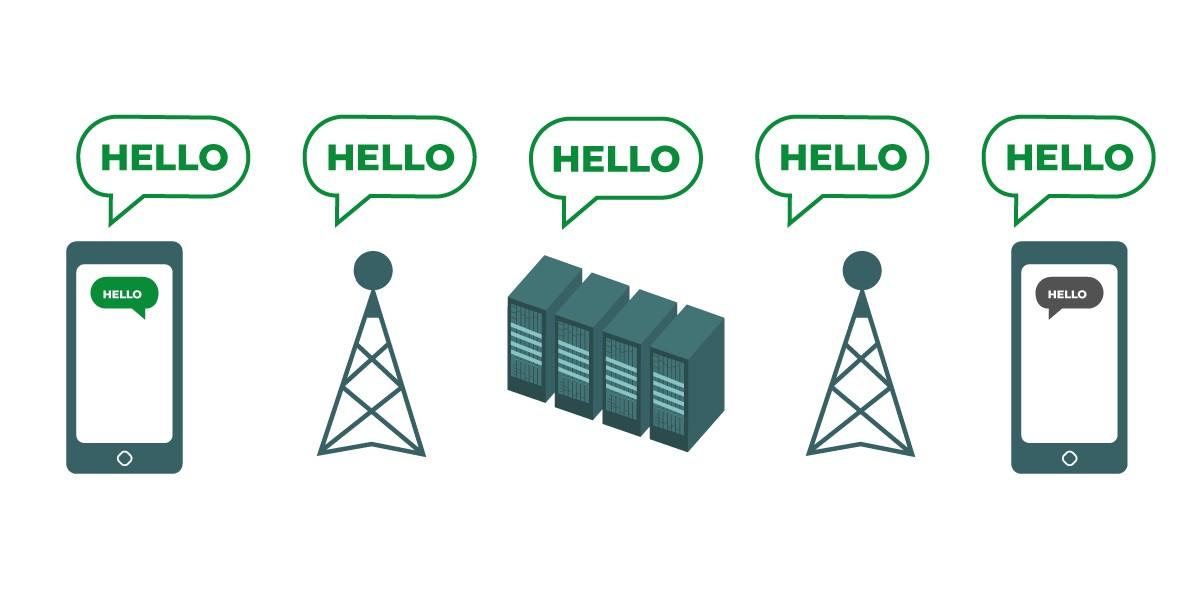
The diagram shows transport-layer encryption. On the left, a smartphone sends a green, unencrypted message: “Hello.” That message is encrypted, and then passed along to a cellphone tower. In the middle, the company servers are able to decrypt the message, re-encrypt it, and send it along to the next cellphone tower. At the end, the other smartphone receives the encrypted message, and decrypts it to read “Hello.” |
Transport-layer encryption, most commonly implemented using the protocol known as transport layer security (TLS), protects messages as they travel from your device to the app’s servers, and then from the app’s servers to your recipient’s device. In the middle, your messaging service provider—or the website you are browsing, or the app you are using—can see unencrypted copies of your messages. Because your messages can be seen by (and are often stored on) company servers, they may be vulnerable to law enforcement requests or leaking if the company’s servers are compromised.
Transport-layer encryption example: HTTPS anchor link

If you inspect the URL bar in your browser, you might see a lock icon, or a menu icon you can click to get a dropdown that shows a lock with a message like, “Connection secure.” This means the website uses HTTPS , an example of transport-layer encryption that we encounter frequently on the web. It provides more security than unencrypted HTTP.
Why?
The servers of an HTTPS website can see the data you enter while on their site (for example, messages, searches, credit card numbers, and logins), but this information is unreadable to eavesdroppers on the network.
If someone is spying on the network and trying to see what websites users are visiting, an HTTP connection offers no protection. On the other hand, an HTTPS connection hides which specific page on a website you navigate to—that is, everything “after the slash.” For example, if you are using HTTPS to connect to “https://ssd.eff.org/en/module/what-encryption” an eavesdropper can only see “https://ssd.eff.org”.
If you’re looking at your browser’s URL and wondering why you don’t see HTTPS or HTTP, that’s because HTTPS is so common these days, many browsers do not even display the full URL by default anymore.
Just because a service uses HTTPS does not mean that the service fully protects the privacy of its users visiting its website. For example, an HTTPS-protected site may still use tracking cookies or host malware .
Transport-layer encryption example: VPN anchor link
A Virtual Private Network (VPN) is another example of transport-layer encryption. Without a VPN , your traffic travels over your internet service provider’s (ISP’s) connection. With a VPN, your traffic still travels over your ISP’s connection, but is encrypted between you and your VPN provider. If someone is spying on your local network and trying to see what websites you’re visiting, they will be able to see that you’re connected to a VPN and who that VPN provider is, but will not see what websites you are visiting.
While using a VPN hides your traffic from your ISP, it also exposes all your traffic to the VPN provider itself. The VPN provider will be able to see, store, and modify your traffic. Using a VPN essentially shifts your trust from your ISP to the VPN, so it’s important to make sure you trust your VPN provider to protect your data.
For further advice on choosing a VPN that’s right for you, read our guide on VPNs.
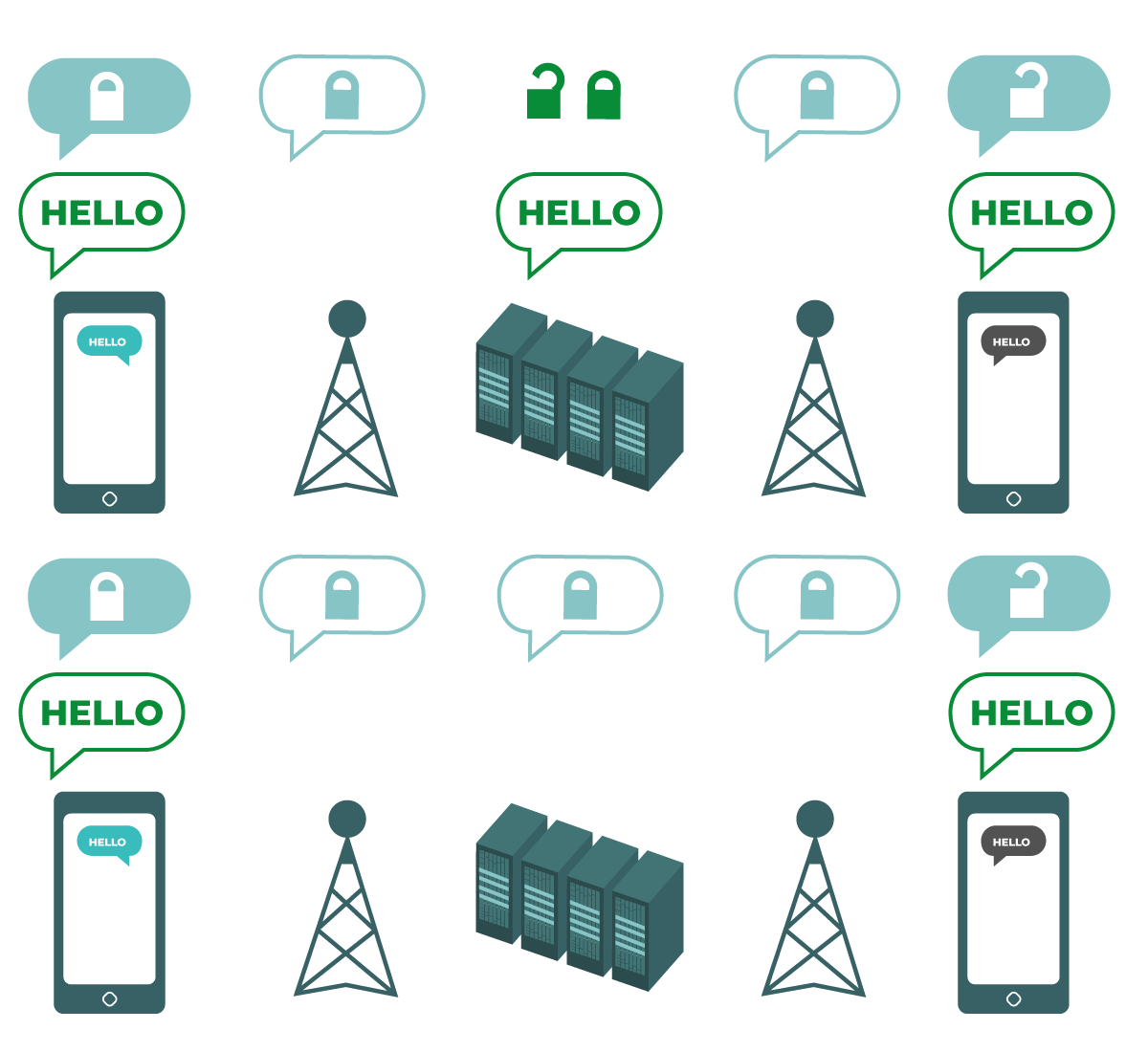
End-to-End Encryption anchor link
|
|
|
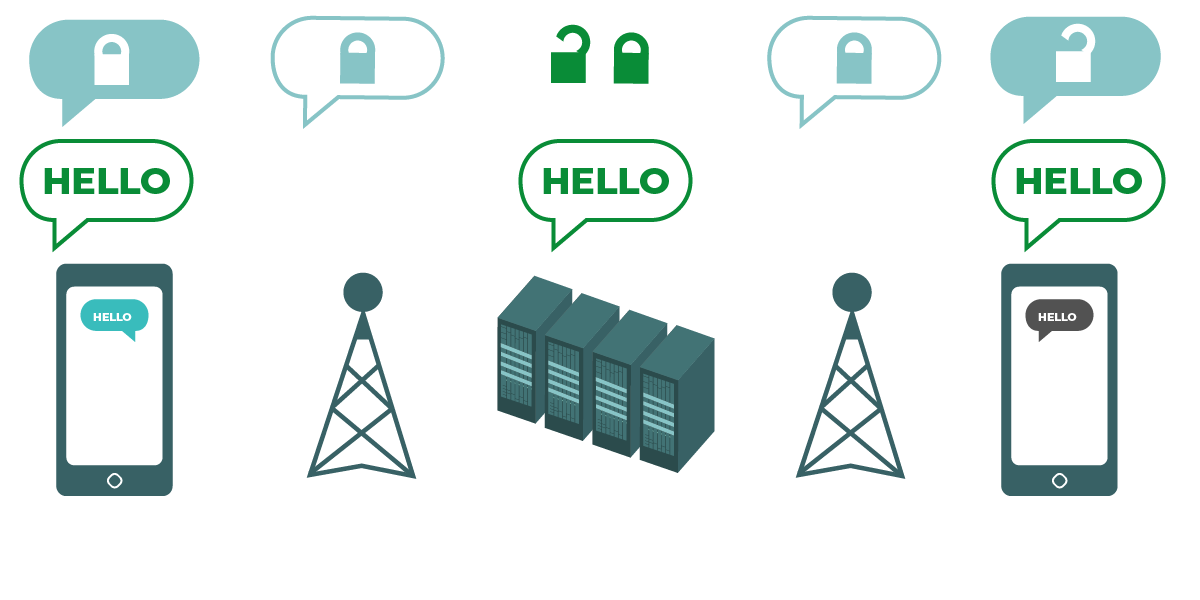
The diagram shows end-to-end encryption. On the left, a smart phone sends a green, unencrypted message: “Hello.” That message is encrypted, and then passed along to a cellphone tower and company servers. At the end, the other smartphone receives the encrypted message, and decrypts it to read “Hello.” Unlike with transport-layer encryption, your ISP’s servers are not able to decrypt the message. Only the endpoints (the original devices sending and receiving encrypted messages) can decrypt the message. |
End-to-end encryption protects messages in transit all the way from sender to receiver. It ensures that information is turned into a secret message by its original sender (the first “end”) and decoded only by its final recipient (the second “end”). No one, including the servers of the app you are using, can “listen in” and eavesdrop on your activity.
Accessing end-to-end encrypted messages in an app on your device means that the app company itself can’t read them. However, while an app developer using end-to-end encryption cannot see the contents of a message, it may still collect certain types of metadata, like what time a message is sent or your IP address .
We offer guides for using end-to-end encryption tools in our Communicating With Others guide and more details about the specifics in our Deep Dive on End-to-End Encryption guide. We also have guides for using two of the most popular chat apps that use end-to-end encryption, Signal and WhatsApp.
Transport-Layer Encryption or End-to-End Encryption? anchor link
Important questions to ask to decide whether you need transport-layer encryption or end-to-end encryption are: Do you trust the app or service you are using? Do you trust its technical infrastructure? How about its policies to protect against law enforcement requests?
If you answer “no,” to any of these questions, then you need end-to-end encryption. If you answer “yes,” then a service that supports only transport-layer encryption may suffice for you—but it is better to go with services that support end-to-end encryption when possible.
What Encryption In Transit Does Not Do anchor link
Encryption is not a cure-all. Even if you are sending encrypted messages, the message will be decrypted by the person with whom you are communicating. If your endpoints (the devices that you are using for communication) are compromised, your encrypted communications can be compromised. Additionally, the person with whom you are communicating can take screenshots or keep records (logs) of your communication.
If you automatically store backups of encrypted conversations to the cloud, be mindful to check that your backups are also encrypted. This ensures your conversations are not only encrypted in transit but also at rest.
If you encrypt data in transit, it will protect the content of your communications, but will not encrypt metadata . For example, you can use encryption to scramble the messages between you and your friend into gibberish, but it does not hide:
- That you and your friend are communicating.
- That you are using encryption to communicate.
- Other types of information about your communication, such as the location, times, and length of communication.
People with heightened surveillance concerns (such as those worried about active monitoring of their networks) can put themselves at risk by only using encryption during sensitive times or for specific activities. Why? If you only use encryption sometimes, it could tie your metadata to important dates and times. It can also reveal that you consider those communications especially sensitive. Therefore, use encryption as much as possible, even for mundane activities.
If you’re the only person using encryption on a network, this metadata may be seen as suspicious. This is why many encryption enthusiasts encourage everyone to use encrypted tools whenever they are able: to normalize the use of encryption for people who really need it.
Putting It All Together anchor link

Together, encrypting both data in transit and at rest will offer you more comprehensive security than using just one or the other. By utilizing multiple methods to defend your data, you can achieve a deeper level of protection. This is what information security experts call “defense in depth.”
For example, if you send unencrypted messages (not encrypting your data in transit) from an encrypted mobile device (encrypting your data at rest), those messages will still be vulnerable to network eavesdropping and interception from governments, service providers, or technically skilled adversaries. The record of the messages on your mobile device, however, will be protected from someone with physical access to your mobile device if they don’t have the passcode.
Conversely, if you send end-to-end encrypted messages (encrypting your data in transit) on an unencrypted device (not encrypting your data at rest), those messages will be safe from snooping and eavesdropping on the network. But someone will be able to access and read the messages if they get physical access to your mobile device.
With these examples in mind, encrypting your data both while it’s in transit on the network and while it’s at rest on your device is ideal for protecting yourself from a wider range of potential risks.
For a deeper dive on how to use encryption, continue onto our guide Key Concepts in Encryption.